BizTalk Server enables companies to automate business processes, through the use of adapters which are tailored to communicate with different software systems used in an enterprise.
In a common scenario, BizTalk enables companies to integrate and manage automated business processes by exchanging business documents such as purchase orders and invoices between disparate applications, within or across organizational boundaries.
Customers trust Microsoft BizTalk to integrate disparate applications and heterogeneous data to deliver solutions such as payment processing, supply chain management, business-to-business EDI, real-time decision making, and reporting.
Sometime, message security becomes a critical factor in integration particularly in Financial and Healthcare domains.
Due to the possible business-critical nature of the messages sent to and from BizTalk Server, it is important to consider measures to help secure these messages and the information they contain both as they are in transit and while BizTalk Server processes and stores them.
BizTalk Server uses the following measures to help secure inbound and outbound messages, to help secure the runtime and configuration information, and to help integrate securely with other applications and systems.
Message security
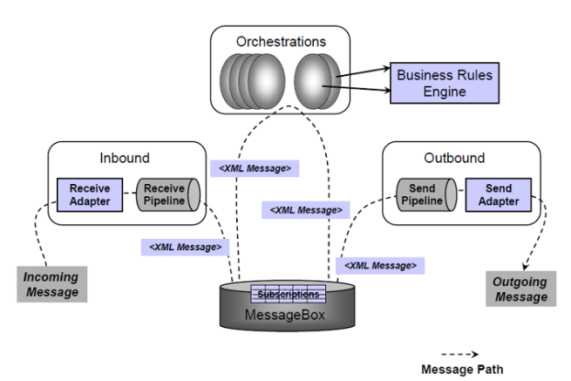
BizTalk runtime architecture primarily has four major components – Receive Handler, Message Box, Orchestration and Send Handler.
Receive handler which is accountable to receive message from channel contains one or more receive locations. Receive location is combination of receive adapter and receive pipeline. Receive pipeline has four stages – Decode, Disassemble, Validate and Resolve Party.
Inbound message can be secured in two ways – Encryption and Digital Signature. These configurations are done at two stages of receive pipeline – Decode and Resolve Party.
BizTalk Server can authenticate the sender of a message (either by using the certificate information or Windows integrated security) in order to validate the identity of the sender of the message.
When BizTalk Server receives an encrypted and signed message, it takes the few steps to ensure that the sending party is recognized. The message authentication details can be found here.
BizTalk Server can also determine what processes and users have permissions to receive the message and it can also enables you to limit the processes and parties that you authorize to receive messages.
Receive authorization is the method you can use to control which hosts can receive (subscribe for) a given message. BizTalk Server uses the certificate information as a subscription property to match predicates on the message: the MessageBox database only routes messages marked as authorization required to the hosts that have the decryption certificate for that message. To illustrate the process, consider the following scenarios:
- Routing an un-encrypted message: When BizTalk Server receives a message that the sender did not encrypt, there is no decryption limitation as to how BizTalk routes the message. Both hosts with and hosts without receive authorization certificates configured can receive the message.
- Routing an encrypted message: When an encrypted message arrives, the receiving pipeline must contain a decoding component that decrypts the message. When BizTalk Server routes a message after it is decrypted, BizTalk uses the certificate thumbprint used to decrypt the message as evidence in the MessageBox database subscription mechanism, and only those hosts configured with that certificate receive the message.
If you want to use receive authorization, you must provide the thumbprint of the decryption certificate in the properties of the host that you want to authorize to receive the message. For more information about receive authorization, see How to Modify Host Properties.
Runtime and configuration security
An approach recommended is to limit the permissions needed by BizTalk to just exactly where they are needed, so if my receive host need to be able to pool a particular SQL Table I should create a BizTalk user account and corresponding Windows Group to assign to the Host and Host Instance that needs that privilege while at the same time only running artefacts in the same host that share the same level of permissions.
BizTalk Server uses access control to ensure that BizTalk Server processes have appropriate limits and that access to business critical information is controlled. In other words, BizTalk Server ensures that users and accounts have the least user rights possible to enable them to do their tasks. For more information, see Access Control and Data Security.
Integrated security
Enterprise Single Sign-On. BizTalk Server uses Enterprise Single Sign-On (SSO) to ensure that it encrypts the sensitive configuration information that the adapters, send, and receive locations require, thus helping to ensure that BizTalk Server stores and transmit this information in a secure manner. For more information, see Essential ESSO in BizTalk.
Related links:
https://msdn.microsoft.com/en-in/library/aa560321.aspx
http://blogs.msdn.com/b/brajens/archive/2006/10/08/message-security-in-biztalk.aspx